
Introduction
Hi everyone! I am back with yet another CTF Challenge called Agent Sudo. Your task is to hack inside the server and reveal the truth. The credit for making this VM machine goes to “Deskel”. There are some Boxes with fun in Tryhackme and trust me, this is one of those boxes. You are going to love it.
You can access this machine from this url: https://tryhackme.com/room/agentsudoctf
After hitting the deploy button we now have our IP address (before starting, check whether the IP is live by pinging ).
#Enum/Recon
Command used: nmap -sS -sV -A -T4 <machine IP>
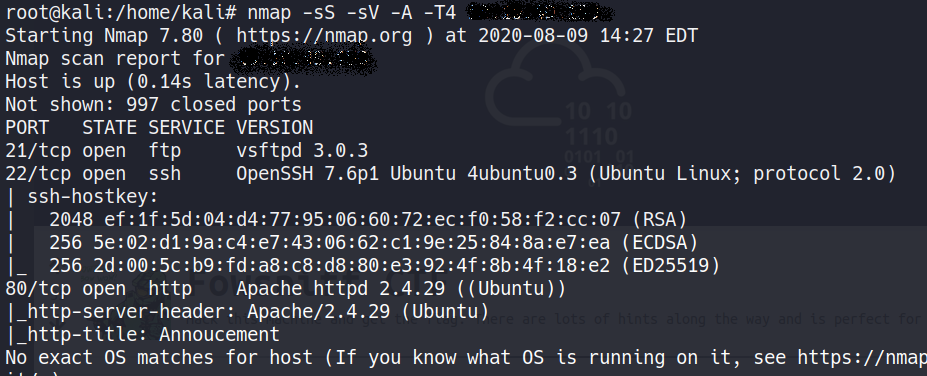
The nmap output shows us that there are 3 ports open, We find that port 80 is running http, so we open the IP in our browser.

So, there is a message to all the other agents from agent R. In Try hack me, there was a hint to check with ‘C’ and I used curl command to check.

#Exploit
Well, as you can see from the above snapshot, we got the username as chris (if i am not wrong!) with the hint that Chris’s password weak…What are we waiting for? Let’s start brute forcing.


Great!!! We found the password, now let’s login to ftp with the credentials.

When we logged in, I just found few files in it and I downloaded those to my local machine.

When I read the To_agentJ.txt file, there was a hint given in the message to dig deeper with the pic files.

#Stegano
I used binwalk tool for searching a given binary image for embedded files and executable code.

It is visible that there is a zip files in the pic file. So let’s extract it
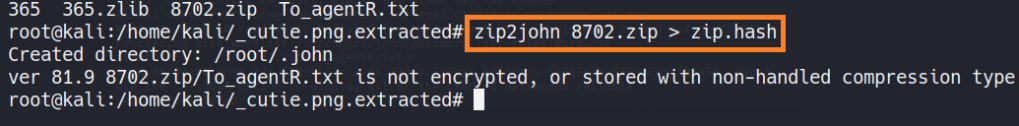
I have used zip2john to extract and cracking the file.

Found the base64 format text and when I decoded it online, found the hidden clue.

Initially when we logged in to ftp, we got two images right? one image was extracted and now it’s time to extract from another image using Steghide.
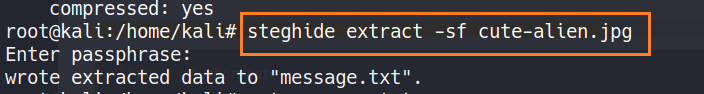
The image was password protected and the password was the one which we decoded from base64 to plain text.
BINGO!! We got the password to connect via SSH.

After successfully logging in, I got the user.txt flag with the .jpg file.

I just downloaded the file to my local machine and googled about the image.


#Priv Esc

It’s time to get the root flag and to get that, as we all know that we should be the root user to acquire. In my previous few boxes I used spawning tty but for this box, I looked for sudo version and downloaded the exploitation script for the same.
script used : https://www.exploit-db.com/exploits/47502
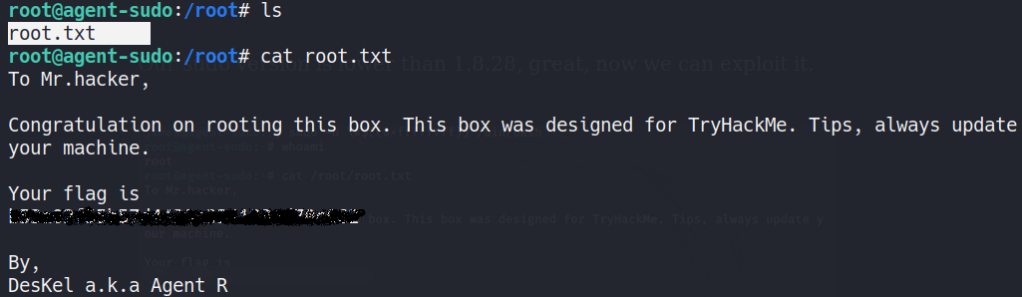

Hallelujah! we got the root.txt flag.
Thanks for reading this writeup too. As I always mention in my every blog, suggestions are always welcome and open for discussion.
Happy Hacking….